In 2019, your website is being scanned within 5 minutes of it existing on the web. If you are not doing anything to protect yourself against at least mass scans you are at risk of having a serious breach.
Why should you do it?
A couple of years ago I noticed that websites I work on get scanned regularly by IP’s from China and Russia. I needed to stop at least some of this behavior or have a real bad problem later when they get a hit.
Since I was using Cloudflare to stand in between the website and the outside world, I wanted to see if I could integrate Cloudflare’s Firewall API to help stop some these mass scans.
There have been a lot of breaches in latest news spanning 5-6 billion records(emails, phones, full names, etc) that could have been prevented by something like this. This measure is to prevent the dumbest scan attacks that might catch you when you are not looking. If you want to know more, check out Have I Been Pwned.
Warning:
This will not stop active attacks and it will also not stop somebody from wanting really to take you down. There is always an answer to whatever your security measures are.
What do you need to get started?
First you will need to have to move your website to Cloudflare DNS. I’m not going to get into this topic here, but you can find tutorial HERE.
Once you have added all the DNS entries and your website is online and working fine, you will need to get your API Authentication Key.
To find it go to:
- 1) My Profile
- 2) Scroll all the way down
- 3) Global API Key -> View
When that is done, you will need to find your 404 page template. Your 404 page usually catches all of these mass scans if they are not caught by Cloudflare WAF. Then paste this code with your email as X-Auth-Email and your Global API key as X-Auth-Key.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 | // CURRENT URL $current_url = $_SERVER['REQUEST_URI']; // GET REAL IP OF USER if (!empty($_SERVER['HTTP_X_FORWARDED_FOR'])) { $ip = $_SERVER['HTTP_X_FORWARDED_FOR']; } elseif (!empty($_SERVER['HTTP_CLIENT_IP'])) { $ip = $_SERVER['HTTP_CLIENT_IP']; } else { $ip = $_SERVER['REMOTE_ADDR']; } // LIST OF WORDS IN URL THAT ARE TRIGGERS FOR CAPTCHA CHALLENGE $attack_list = "/phpmyadmin|PMA|administrator|myadmin|mysql|xdebug|appserv|cmd|hello|webdav|typo3|cacti|dbadmin|hell|mysql|godkey|joomla|xampp|python|xdebug|thinkphp|hack|drupal|fxcodeshell|payload|struts|composer|lol|knal|java|lala|pma-old|w00tw00t|anti-sec|wp-config|wp-content|xampp|sheep|_query|db__|login.cgi|mysqladmin|sql|cmd|java|dbadmin|union|select|sleep|wait|character_sets|delay|group|schema|webdav|fack|chmod|dbadmin|wget/"; if (preg_match($attack_list, $current_url)) { cfban($ip, $current_url); } // CONNECT TO CLOUDFLARE AND SEND THEM DETAILS OF ATTACKER function cfban($ipaddr, $current_url) { $cfheaders = array( 'Content-Type: application/json', 'X-Auth-Email: YOUR_EMAIL', 'X-Auth-Key: YOUR_GLOBAL_API_KEY' ); $data = array( 'mode' => 'challenge', 'configuration' => array('target' => 'ip', 'value' => $ipaddr), 'notes' => 'Challenge on ' . date('Y-m-d H:i:s') . ' by PHP-script - BAD GUY' . ' url: ' . $current_url . ' .' ); $json = json_encode($data); $ch = curl_init(); curl_setopt($ch, CURLOPT_POSTFIELDS, $json); curl_setopt($ch, CURLOPT_RETURNTRANSFER, true); curl_setopt($ch, CURLOPT_HTTPHEADER, $cfheaders); curl_setopt($ch, CURLOPT_URL, 'https://api.cloudflare.com/client/v4/user/firewall/access_rules/rules'); $return = curl_exec($ch); curl_close($ch); if ($return === false) { return false; } else { $return = json_decode($return, true); if (isset($return['success']) && $return['success'] == true) { return $return['result']['id']; } else { return false; } } } |
This will make an entry in Cloudflare’s firewall “Tools” tab to challenge the IP address on next visit.
It will look something like this:
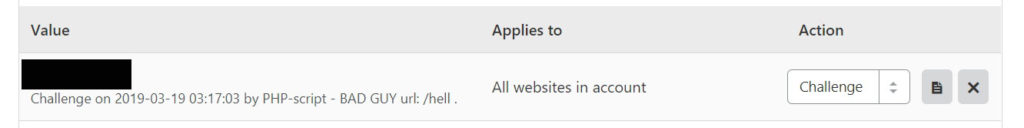
It will have visitor’s:
– IP address
– Time they visited
– URL they requested
My plan is to later on to add POST contents into the Cloudflare notes too to see what exactly they were trying to POST or GET.
Why CAPTCHA challenge instead of BAN?
I would recommend just using Challenge mode in case some of these strings are in your valid URL’s or your customers mistakenly enter them into URL.